TL;DR — What You'll Learn
Comprehensive guide to cloud security best practices and strategies to protect your cloud infrastructure...
Cloud Security is a combination of controls, processes, and programs that safeguard your cloud-based systems, data, and structure. It encompasses computer security and information security, and your cloud service provider should have a strategy in place to protect your data, comply with regulations, and ensure your privacy.
Cloud Security protects you from the negative impacts of data breaches and loss, such as financial and legal consequences and damage to your reputation. Nowadays, the Best mobile app development companies in Hyderabad use cloud services or infrastructure in the form of SaaS (Software as a Service), IaaS (Infrastructure as a Service), and PaaS (Platform as a Service).
Why is Cloud Security Important?
Top Mobile Application Development in Hyderabad migrates its data, applications, and other assets to cloud security, so it becomes increasingly crucial to understand how to safeguard this highly sensitive business information that could potentially be exposed.
For so many industries, regulatory compliance is another main reason cloud security is very important. They must comply with strict standards, or else they risk huge fines.
Amongst the respondents:
- 35% admitted that they're high-quality recommendations about the security of public cloud or hybrid cloud
- 41% were very concerned
- 23% were moderately or slightly concerned
- Only 1% said they were not at all concerned
What is the Cloud Security Alliance?
In the cloud computing industry, there is no central governing body to guide businesses facing challenges such as cloud security. However, there are several associations dedicated to supporting the industry. One similar association is the cloud security alliance.
Thankfully, in the place of governing bodies, several associations devote themselves to supporting the industry. The Cloud Security Alliance is one similar association.
It is a membership association offering the industry cloud-specific security guidance in the form of education, exploration, events, and products. It offers cloud-specific security guidance through education, exploration, events, and products.
What is Cloud App Development
Cloud App Development, also called cloud development or cloud computing development, refers to the process of designing, developing, deploying, and managing operations that leverage the power of cloud computing structure. In simpler terms, it is the practice of creating software results that run on remote servers, rather than on original biased or on-demesne servers.
If you imagine a mobile app development company that operates independently, requiring its maintenance, and staff security. Cloud App Development, fantasize about an ultramodern recreation demesne where all the lifts partake in a centralized power source, conservation team, and staff. This setup is more effective, cost-effective, and easier to manage. This is similar to cloud development, where operations are built, deployed, and maintained on shared participating remote waiters handed by all service providers.
Some of the Security Risks of Cloud Computing
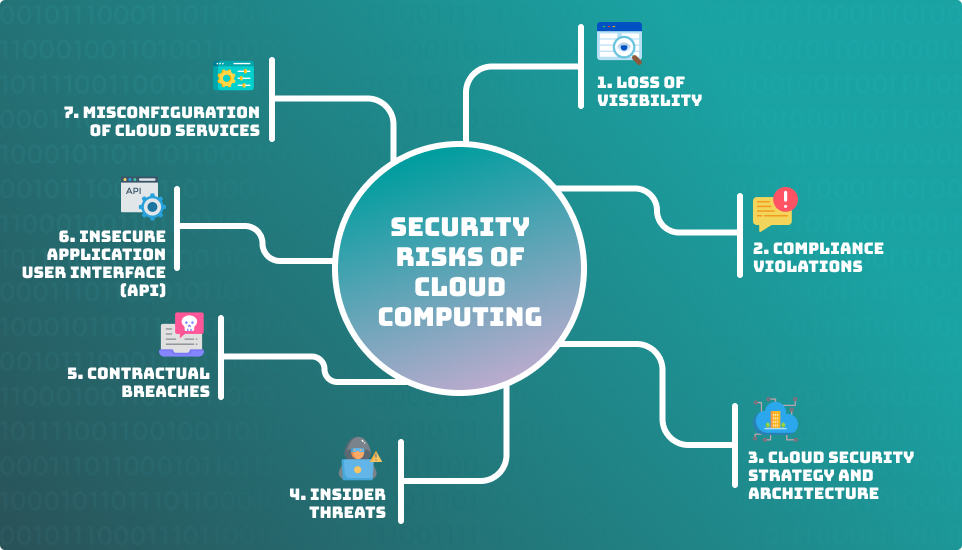
Security is a crucial concern for businesses, regardless of whether they operate in the cloud or not. There are various risks that businesses may face, such as denial of service, malware, SQL injection, data breaches, and data loss.
- Loss of Visibility
Firstly, the complexity of accessing cloud services through different devices, departments, and locations can cause a loss of visibility.
- Compliance Violations
Compliance violations can occur if businesses fail to adhere to regulatory requirements while moving to the cloud.
- Cloud Security Strategy and Architecture
A lack of cloud security strategy and architecture can lead to insider threats, which can cause damage to businesses.
- Insider Threats
Misconfiguration of cloud services can expose data, manipulate or delete it. This is a growing issue due to the increasing range and complexity of cloud services.
- Contractual Breaches
Any contractual Breaches you have will include restrictions on how the data is shared and used, how it is stored, and who is authorized to access it.
- Insecure Application User Interface (API)
APIs built into web or mobile applications can offer internal access, which can be a potential security risk. It is essential to ensure an API's secure application user interface.
- Misconfiguration of Cloud Services
Misconfiguration of cloud services is another big risk of cloud security. With the complexity of services, this is the main growing issue of cloud services.
How Can mTouch Labs Assist You In Tightening Your Cloud Security?
Suppose you have to need a top cloud security strategy if you're moving to the cloud. Hence, make sure to choose the cloud service provider precisely. So, ensure to apply the forenamed cloud computing security best practices to enhance the security of your cloud computing system.
You can indeed hire the best cloud service provider , like mTouch Labs, to work dedicatedly to take care of your cloud ecosystem and its security. So, Are you looking for cloud services?
Let us know your requirements for Our Best Mobile App development company in Hyderabad.
How can mTouch Labs help you with Cloud App Development?
mTouch Labs is a Cloud app development company that focuses on software development. Their professional team of mobile app developers company in Hyderabad and engineers can assist firms in designing, building, and deploying software apps on cloud platforms including AWS, and Google Cloud Platform. mTouch Labs provides various services, including cloud consulting, application development, testing, developing, and maintenance.
Conclusion
Scalability, reliability, cost value, flexibility, and security are the best advantages of the cloud application development process. mTouch Labs provides you with the best in Planning, designing, developing, testing, deployment, and maintenance are all required steps in a secured top development process.



